XSS Vulnerability report for PPTX2HTML (En)
mer. 02 janvier 2019 Dan Lousqui
(Note: when I say things like bad practice, not enough security or insecure, it is not against any developer.
Security is something complex, and it is very hard to see its own flaws. I am grateful for all open-source developers
work, and this article is just about reporting, learning and self-improvement.)
(Note 2: this article will be updated for new data, as it occurs)
PPTX2HTML is a library used by some projects in order to convert PPTX files
into HTML documents. A PPTX file is a complex file format composed of:
XMLfiles containing data, references, styling and many other informations;- binary files, for objects, images and other data;
- All of it, compressed into one file in
ZIPformat.
Converting PPTX to HTML
In order to convert a PPTX file into HTML, PPTX2HTML do the following :
- Unzip the file (as the
.pptxis in aZIPformat) ; - Interpret the
XML; - Generate an
HTMLnode using retrieved data.
Unzipping is performed using the Stuk/jszip library, I did not find anything relevant on that part.
Interpreting the XML is performed using TobiasNickel/tXml library, I did not
find anything relevant on that part (I was looking for XXE / XML Bomb / JS injection).
However, the HTML generation is not performed with enough security measures, leading to
Cross-Site Scripting (XSS) flaws (more info).
Generate HTML
Cross-Site Scripting flaws occurs when HTML or Javascript are generated from user generated input and are nor parsed nor escaped with security precaution. The could lead to session stealing, execution of malicious code, HTTP tunnel and many other malicious events (more info).
PPTX2HTML generate HTML using concatenation. It is a bad practice because you need to escape / unescape strings in many tricky ways.
For exemple, in order to generate a link, PPTX2HTML use the following snippets (github ref.):
var linkURL = warpObj["slideResObj"][linkID]["target"];
return "<span class='text-block " + cssName + "'><a href='" + linkURL + "' target='_blank'>" + text.replace(/\s/i, " ") + "</a></span>";
If linkURL as a standard value, such as https://google.com, the generated HTML will be:
<span class='text-block foo'>
<a href='https://google.com' target='_blank'>
bar
</a>
</span>
However, if linkURL has a maliciously crafted URL, such as '></a><img src='b' onError='alert("XSS !")'><a a=', the
generated HTML will be:
<span class='text-block foo'>
<a href=''></a>
<img src='b' onError='alert("XSS !")'>
<a a='' target='_blank'>
bar
</a>
</span>
This code will execute the Javascript code alert("XSS !") (which can be changed to anything malicious).
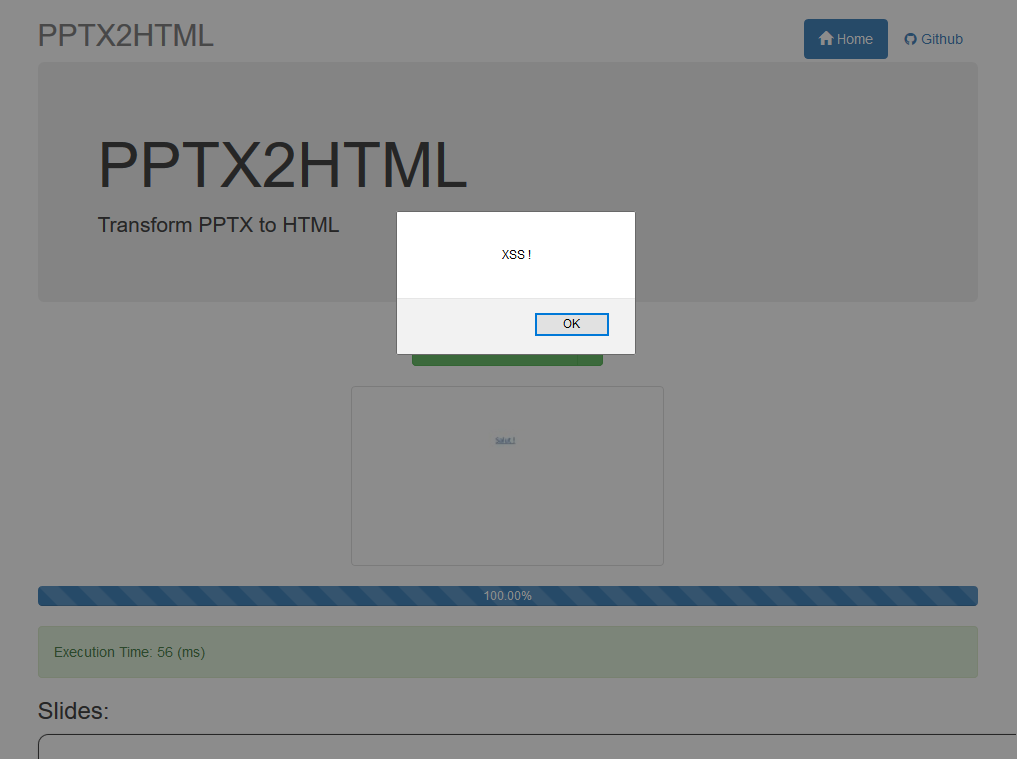
Proof
You can try this exemple using this file, using that exact same payload.
You can test the PPTX2HTML library online here: http://g21589.github.io/PPTX2HTML/, it will give the following result:
Timeline
- 2018-11-27 : Vulnerability found
- 2018-11-27 : Original author (g21589) contacted
- 2018-11-27 : Github Issue created contacted
- 2018-11-27 : Reported on npm registry
- 2018-12-04 : NPM reached out the maintainer
- 2018-12-07 : NPM published an advisory (but I did not manage to find it ...)
- 2019-01-02 : Releasing this report
